It has been almost seven years since I last played with IPv6 (
link,
link). There has been lots of talk of IPv6 lately, and the
company I work for has done some real-world IPv6 testing and deployment (check out Tore's IPv6 page:
http://fud.no/ipv6/).
Since my local ISP has not deployed IPv6, and probably will not for a long time - I went looking for a "IPv6 tunnel broker". A tunnel broker enables you to tunnel IPv6 traffic over IPv4 to a IPv6 gateway (called "PoP").
So, which tunnel broker to choose from? Wikipedia give me a
lot of choices. Several colleagues tipped me of
SixXS -- their service is stable and professional, you get a /48 network and they have a PoP here in Oslo they said. Easy choice.
First some paperwork:
1) First, apply for an account at SixXS:
http://www.sixxs.net/signup/create/
Be patient - this can take some time since it require manual (human) verification. It took me 8 hours from I applied to my account was accepted.
2) Once you get your username and password, log into the web-interface, and proceed to request a tunnel. Choose
"Dynamic NAT-traversing" as type of tunnel. Choose your neares POP, and submit. This process is automated, and it took approx 30 minutes before my request was accepted.
3) When 2) is complete - you have ONE routable IPv6 address. Since we need more than that, we proceed to request a subnet from SixXS webpage. 30 minutes later, my subnet was allocated.
So I've received from SixXS the following information (not actual IPv6 addresses):
A) IPv6 gateway at SixXS:
2001:FFFF:FFFF:FFF::1/64
B) My local IPv6 gateway:
2001:FFFF:FFFF:FFF::2/64
C) My allocated IPv6 subnet, which is routed to B):
2001:FFFF:EEEE::/48
Next, we're ready to configure/install:
4) First, install a helper daemon that take care of your IPv6 tunnel automatically. It's called
AICCU (Automatic IPv6 Connectivity Client Utility):
http://www.sixxs.net/tools/aiccu/
On Debian/Ubuntu install it by:
$ sudo apt-get install aiccu
Enter your SixXS username and password when asked for it. You tunnel interface will be named "sixxs" and enabled (global IPv6 address in red):
$ ifconfig sixxs
sixxs Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet6 addr: fe80::14d8:eeff:142:2/64 Scope:Link
inet6 addr: 2001:FFFF:FFFF:FFF::2/64 Scope:Global
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1280 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:3 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 B) TX bytes:144 (144.0 B)
5) Test your IPv6 connection:
$ ping6 ipv6.google.com
PING ipv6.google.com(2a00:1450:8004::93) 56 data bytes
64 bytes from 2a00:1450:8004::93: icmp_seq=1 ttl=52 time=42.5 ms
64 bytes from 2a00:1450:8004::93: icmp_seq=2 ttl=52 time=44.0 ms
64 bytes from 2a00:1450:8004::93: icmp_seq=3 ttl=52 time=43.7 ms
...
Good, we have IPv6 connectivity, but only from one host. We want IPv6 on our whole home network.
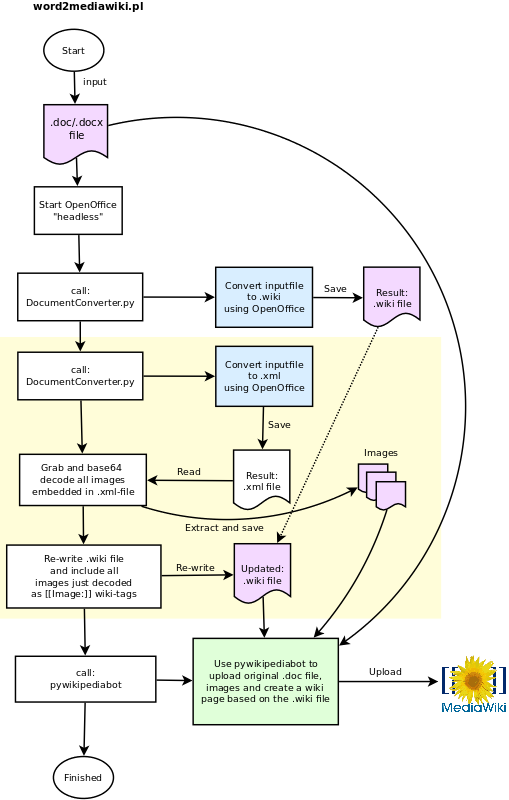
6) Since we're given a /48 network, it enables us to have 65536 /64 networks. Which should suffice for most needs. Our network architecture would look like this when complete:
We configure our IPv6 gateway (vallhall-r6) to route IPv6 traffic for our local network. First we need to assign a IPv6 address on the actual interface facing our network. This will be our IPv6 gw address for our network:
$ sudo ifconfig eth0 inet6 add 2001:FFFF:EEEE::1/48
$ ifconfig eth0
eth0 Link encap:Ethernet HWaddr 52:54:de:ad:be:ef
inet addr:192.168.1.100 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::5054:ff:feb6:beef/64 Scope:Link
inet6 addr: 2001:FFFF:EEEE::1/48 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:16849 errors:0 dropped:0 overruns:0 frame:0
TX packets:13394 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:7336450 (7.3 MB) TX bytes:7082583 (7.0 MB)
Make it permanent by adding it to:
# cat /etc/network/interfaces
...
iface eth0 inet6 static
address 2001:FFFF:EEEE::1
netmask 48
endpoint 2001:FFFF:FFFF:FFF::1 # your SixXS gw
ttl 64
7) Make sure our gateway route IPv6 traffic:
$ sudo sysctl net.ipv6.conf.all.forwarding=1
net.ipv6.conf.all.forwarding = 1
Make it permanent, by adding it to:
$ cat /etc/sysctl.conf
...
net.ipv6.conf.all.forwarding=1
8) You can now configure your network equipment with static IPv6 addresses. Since IPv6 uses hex (and thereby the letters A-F), some words/sentences can be embedded in these addresses:
baba, babe, bade, bead, beef,
cede, dace, dada, daff, dead,
deaf, deed, face, fade, feed, ...
This way, your file-server can have an address like:
...:daff:bade:babe
go wild..
9) We don't want to configure all our host manually, so we need some kind of auto-configure. While IPv6 have DHCPv6, (like IPv4's DHCP), a more elegant solution is to use
"stateful address autoconfiguration".
The host configure themselves by acquiring a prefix from a local IPv6 router, and combined with the local MAC address, creates a IPv6 address (router advertisements + MAC address of interface = IPv6 address).
We use radvd for sending these "router advertisements". Install and configure:
$ sudo apt-get install radvd
$ cat /etc/radvd.conf
interface eth0 {
AdvSendAdvert on;
MinRtrAdvInterval 3;
MaxRtrAdvInterval 10;
prefix 2001:FFFF:EEEE:aaaa::/64 {
AdvOnLink on;
AdvAutonomous on;
# After testing, can be set to 14400
AdvPreferredLifetime 30;
# After testing, can be set to 86400
AdvValidLifetime 30;
};
};
Start radvd:
$ sudo service radvd restart
Stopping radvd: radvd.
Starting radvd: radvd.
10) Excellent! Radvd will now send IPv6 prefix periodically (or when requested by a new client) to your network. All IPv6 capable host should now automatically configure themselves with a IPv6 address.
You should now be able to access IPv6 enabled hosts. Try for example:
http://ipv6.google.com
11) A final warning and advice:
ADD A FIREWALL on your IPv6 gateway! Since IPv6 don't use NAT, every hosts that use IPv6 is
directly accessable from the Internet. This is a good thing, but it also expose all your IPv6 enabled hosts and their services.
A good starting point for IPv6 firewall:
https://www.sixxs.net/wiki/IPv6_Firewalling
Good luck!
Troubleshooting tips:
I) Dump IPv6 traffic using tcpdump:
# tcpdump -i eth0 -vv ip6 or proto ipv6
II) Show your IPv6 routing table:
# ip -6 r s
II) Check radvd messages
# radvdump